Advanced automated cyber security testing
Programme
GSTP
Programme Reference
GT1Y-310GD
Prime Contractor
PROXIMUS LUXEMBOURG S.A.
Subcontractors
TELESPAZIO VEGA DEUTSCHLAND GMBH
Germany
Start Date
End Date
Status
Contracted
Country
Luxembourg
Objectives
The objective of the activity is to develop an automated security and penetration testing framework with associated fully representative and modular test environment in order to enhance the secure system development lifecycle with effective security testing capabilities.
Description
In today?s increasingly connected and contested cyber space, effective and thorough security testing of software and systems is mandatory to achieve any level of security assurance and trustworthiness of systems for its stakeholders. In fact many organizations and owners of modern complex systems today adopt a paradigm of ensuring system resilience rather than prevention and protection, assuming that attacks and some level of compromise are inevitable and focusing on how to minimize associated disruption.
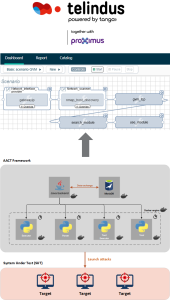
Security testing at the level of disruptive penetration testing and code scanning is required by the ESA Secure Software Engineering Standard. Penetration testing in particular however is a highly-specialized, effort-intensive and expensive exercise. To allow for cost-efficient yet reliable and realistic testing, ESA has recently developed a prototype demonstration and successful proof of concept of an automated penetration testing framework ?Penbox?.
This activity shall build upon the PenBox prototype, with the objective to provide a stable automated security testing and user awareness-building capability for new ground segment software and system developments.
In particular this activity encompasses the following tasks:
- Improve the stability, performance and reporting capabilities of the PenBox prototype;
- Enhance with additional penetration testing tools and attack capabilities, specifically targeting space-specific systems and protocols;
- Develop a robust and re-usable tool execution, results parsing and logic sequences for automated security requirements verification;
- Build upon existing executable attack scenarios, tailored for real space mission system configurations, from both a blackbox and whitebox perspective;
- Develop the user interface and user capability to edit and tailor attack scenarios and requirements verification;
- Integrate with other secure systems engineering tools and developments (e.g. risk assessment and requirements management tools) to support the secure development lifecycle through continuous security testing;
- Future steps including ways to exploit artificial intelligence and machine learning capabilities to drive automated security tests.
Disruptive security testing cannot be executed on operational systems. A fully-representative test environment is required. Therefore in addition, this activity shall:
- Analyse the suitability of existing ground segment and system laboratories (for example the ESA Cyber Range in ESEC, the Ground Segment Reference Facility in ESOC, the virtualized PenBox testing environment);
- Inter-connect the different labs and configuration and deployment systems as required to realize a fully representative test environment for an end-to-end space mission system;
- Develop a maintenance and system deployment concept, building upon existing capabilities and technologies such as VMWare, Jenkins, Docker, Chef etc. in order to enable a flexible security testing service for new system developments.
Finally, scenario and requirement verification tests shall be conducted using the enhanced PenBox application and representative environment. A critical report shall be produced analyzing the tool?s effectiveness, usability, coverage and cost benefit verses traditional manual or out-sourced penetration testing approaches.
Application Domain
GEN-Generic Technologies
Technology Domain
8-System Design & Verification
9-Mission Operation and Ground Data Systems
Competence Domain
9-Digital Engineering
Keywords
48-Cybersecurity
Initial TRL
TRL 4
Target TRL
TRL 6
Achieved TRL
TRL 6
Public Document
Executive Summary
Final Presentation
